Anatomy of an AI-Powered Terraform PR Review: What Your Platform Team Gets on Every Pull Request
TL;DR
- Terracotta AI runs 12 automated checks on every Terraform PR automatically, the moment it's opened
- Every check posts directly in your PR comment: changes summary, simulated plan, code review, guardrails, conflict detection, drift detection, cost impact, IAM security, tag compliance, blast radius, dependency mapping, and architecture diagrams
- No Rego, Sentinel, OPA, or custom scripts connect your repo, and it works
- Works with GitHub, GitLab, and HCP Terraform Run Tasks
- Your team stops rubber-stamping plans and starts approving with confidence
Your platform team is reviewing more Terraform PRs than they can safely handle. Every week, there are more infrastructure changes, more modules, more environments, and the same three engineers rubber-stamping plans because they don't have time to actually read them. The blast radius gets missed, the drift gets ignored, and the security group that's open to the world gets approved because it's PR number fourteen that day, and everyone's already in the next sprint.
Nobody on your team feels confident about hitting the approve button. They just don't have a choice.
You've been here. Your team has been here. And the incident that finally forces the conversation is always the one that could have been caught in the PR if anyone had the time and context to catch it.
This is what a single Terraform PR looks like after Terracotta AI reviews it:
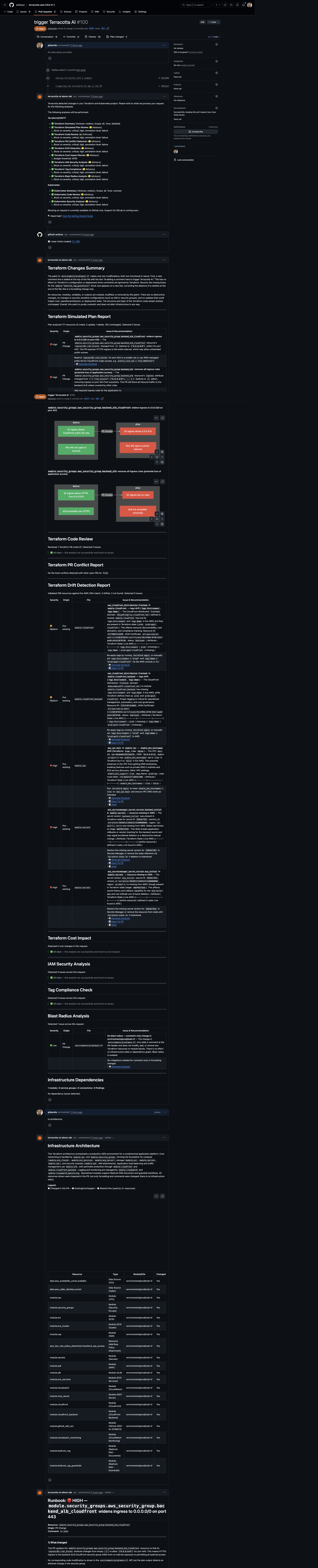
One PR. One comment. Twelve automated analysis sections covering everything from simulated plan analysis and drift detection to IAM security, cost impact, blast radius, dependency mapping, and a full infrastructure architecture diagram. All of it runs automatically the moment a PR is opened. No Rego. No Sentinel. No custom scripts. No pipeline changes.
Let’s break down what’s happening, section by section.
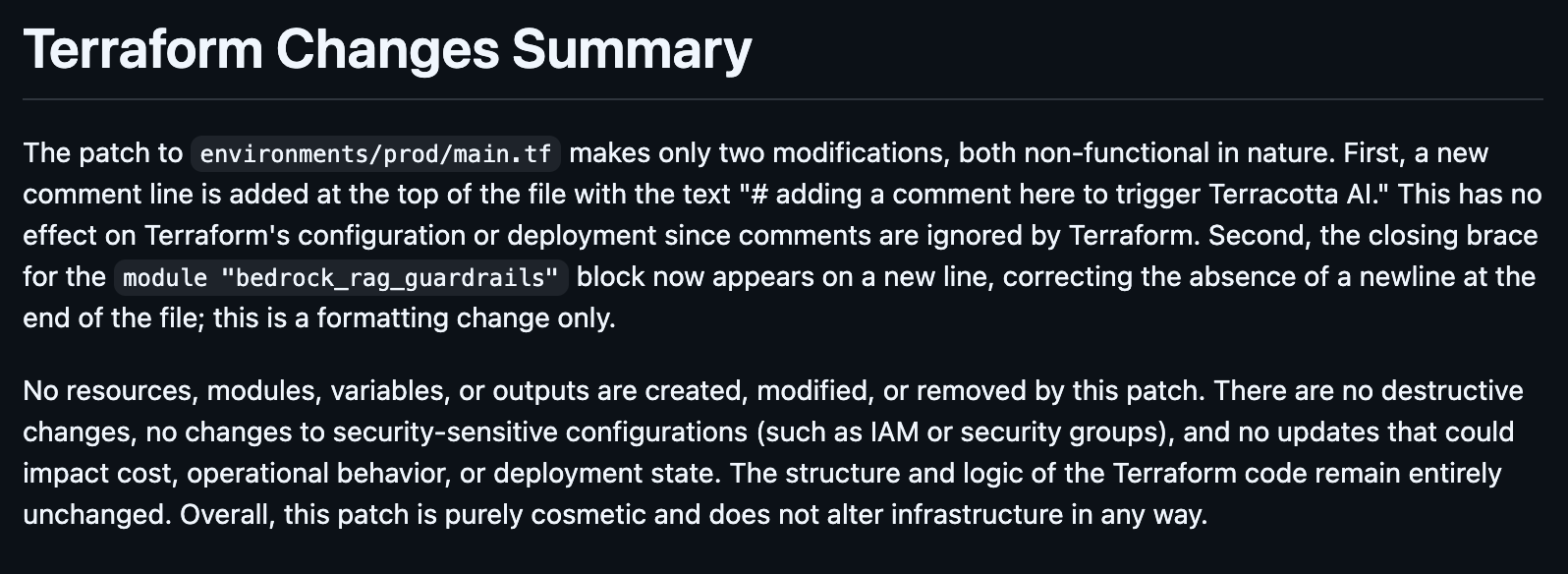
Terraform Changes Summary
The first thing your reviewer sees isn’t a raw diff or a wall of HCL. It’s a plain-English summary of what this PR actually does, which resources are being created, modified, or destroyed, and why it matters.
This is the “here’s what you need to know before you look at anything else” section. It gives your team immediate context without parsing the diff line by line. For a senior engineer reviewing their tenth PR of the day, this is the difference between a 30-second triage and a 15-minute deep dive into code they didn’t write.
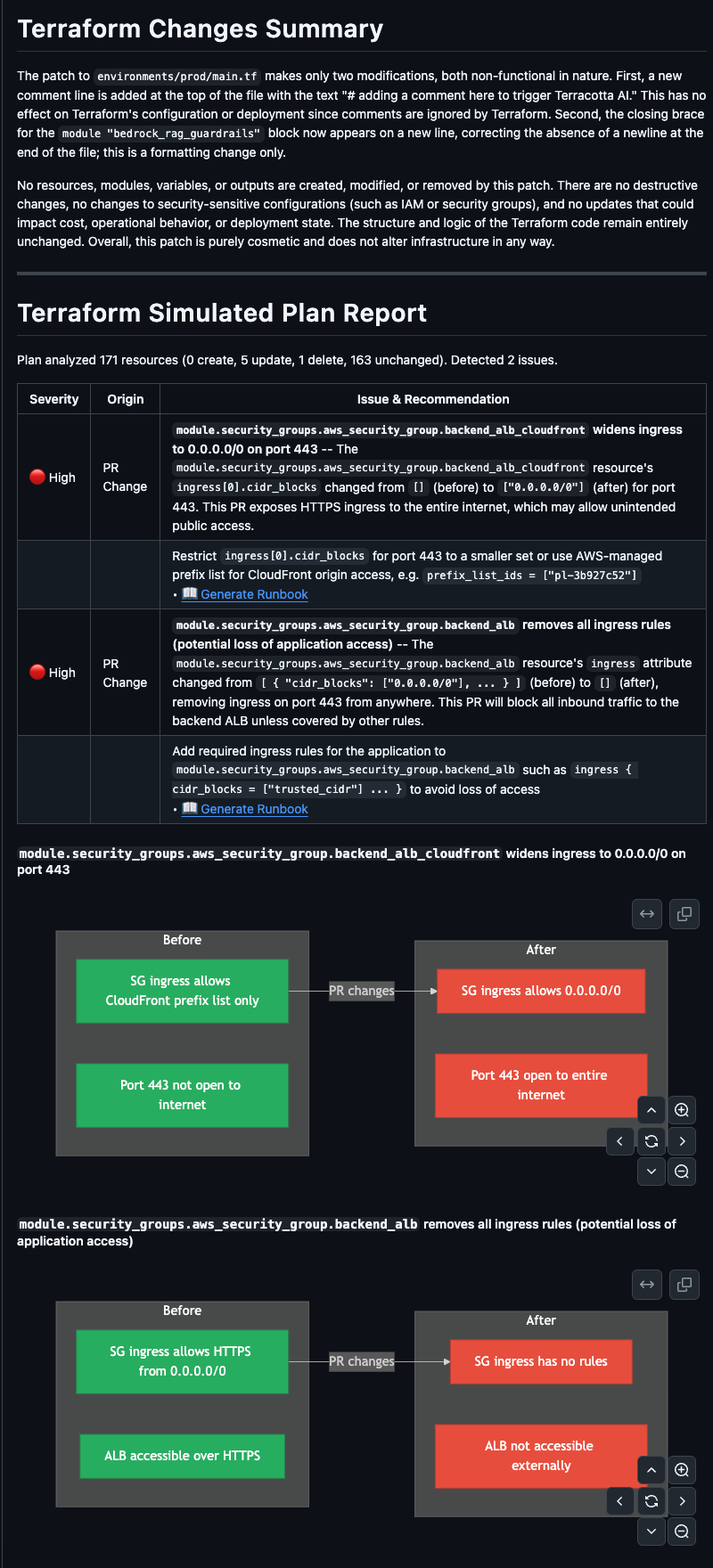
Terraform Simulated Plan Report
This is where Terracotta AI diverges from every other code review tool on the market. We don’t just look at the code diff; we simulate what Terraform will actually do when this code runs.
The Simulated Plan Report shows a resource-level breakdown of planned actions: what’s being created, what’s being updated in place, and what’s being destroyed and recreated. Each resource is displayed with its action type, resource address, and the specific attributes being changed. The report includes visual diagrams showing how resources relate to each other within the plan, so you’re not just seeing a list of changes, you’re seeing the shape of the change.
This is the plan output your team would normally only see after running terraform plan in CI. Terracotta AI surfaces it directly in the PR comment, before anyone approves anything, with context and explanation that a raw plan output can never provide.
Terraform Code Reviews
Line-level code review findings on the Terraform changes in the PR. These aren’t generic linting rules; they’re contextual findings that understand what the code is doing in the context of your existing infrastructure.
Each finding includes severity, the affected resource, a clear explanation of the issue, and a recommended fix. Findings eligible for automated fixes include committable suggestions and one-click fixes that your engineers can apply directly from the PR without leaving GitHub or GitLab.
Your junior engineers get senior-level feedback on every PR. Your senior engineers stop repeating the same review comments across dozens of PRs every week.
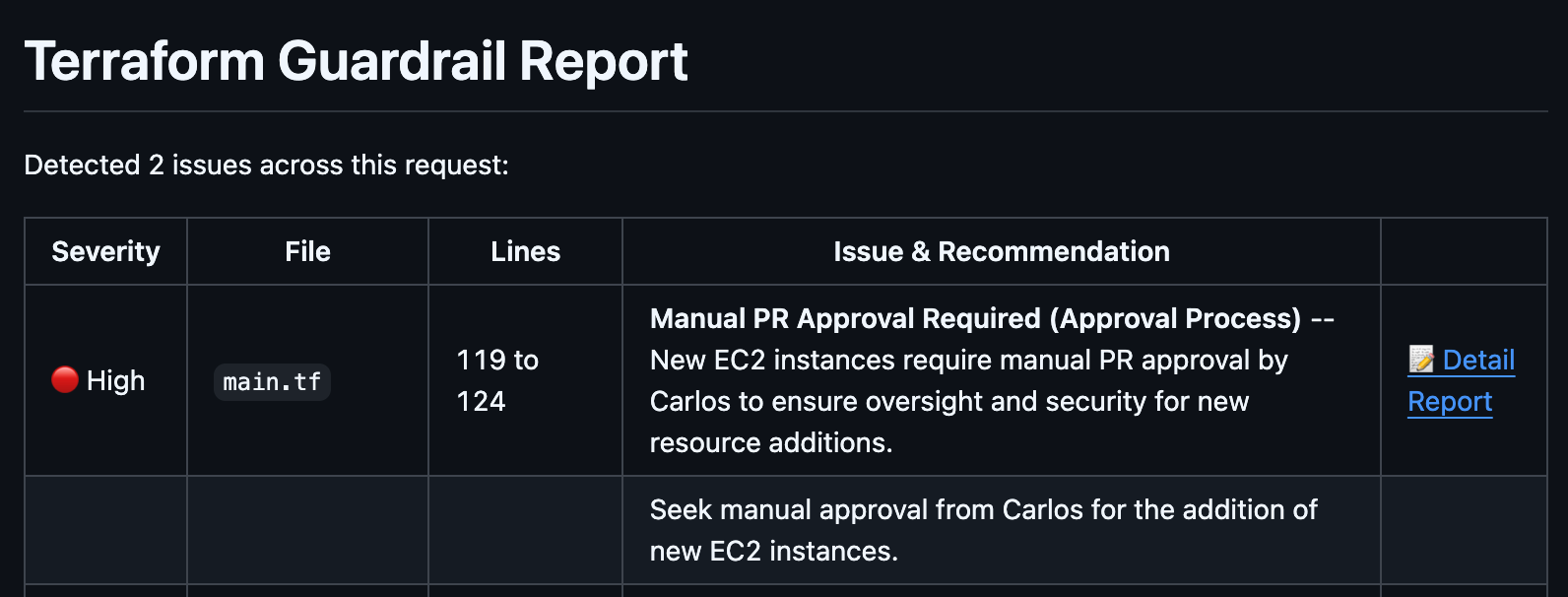
Terraform Guardrail Report
Platform teams have standards. You may require encryption on every S3 bucket. Maybe you don’t allow public subnets in production. Maybe your security team mandates specific tagging conventions or instance types for compliance.
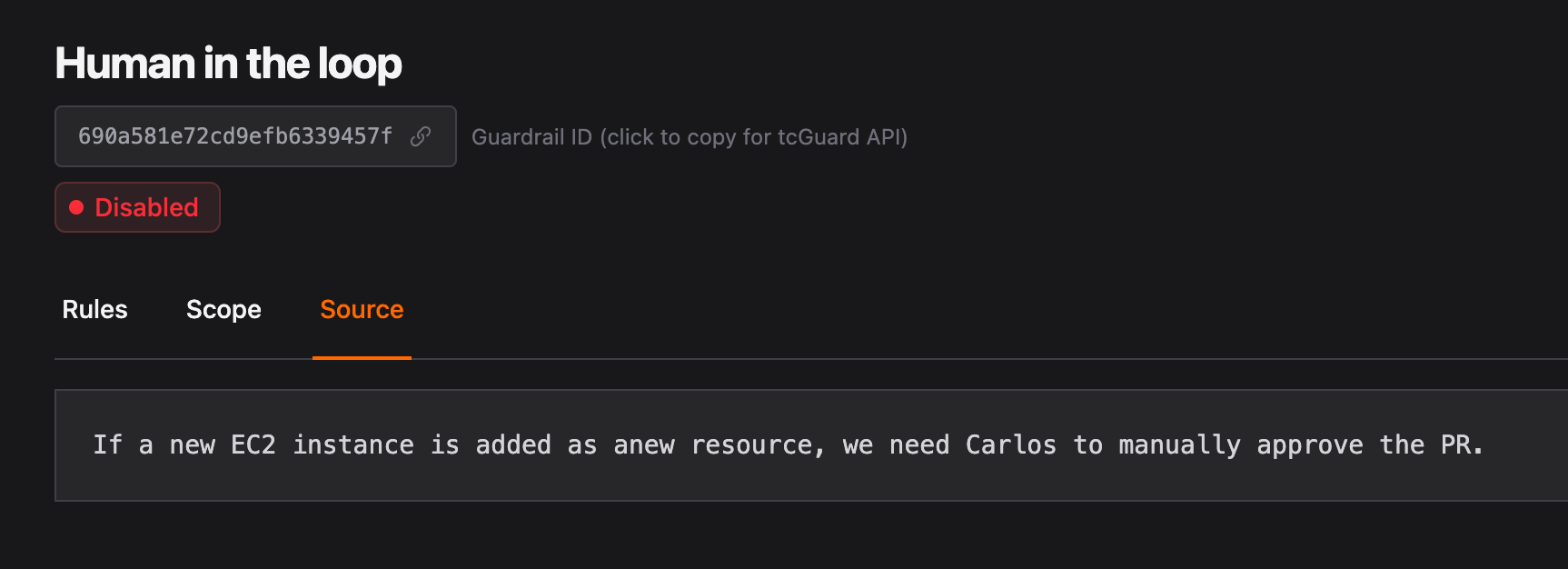
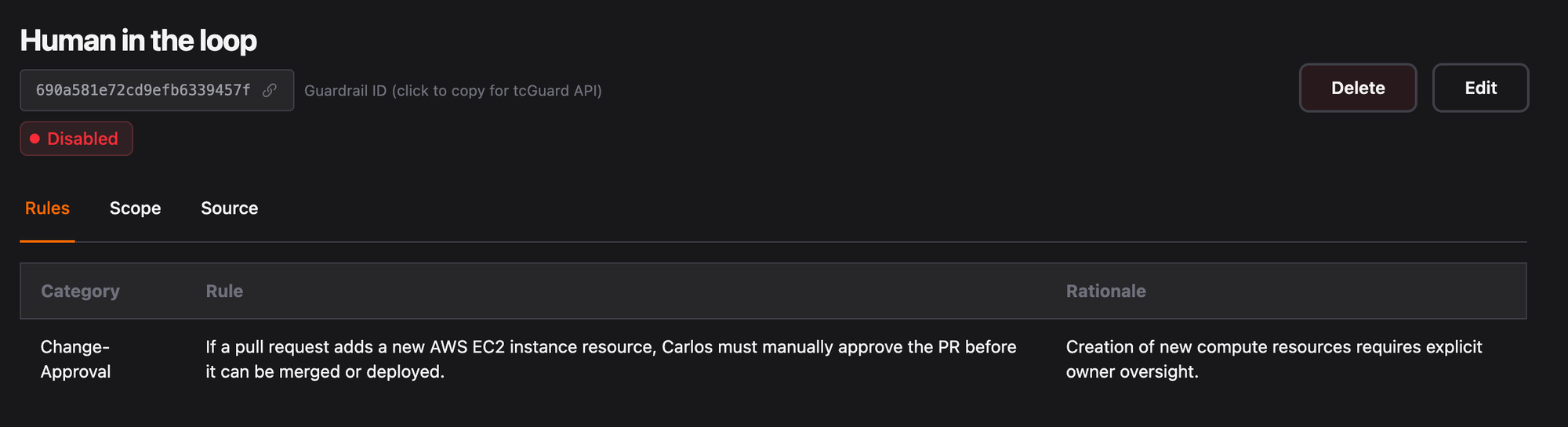
Terracotta AI Guardrails let you define these policies in plain English. No Rego. No Sentinel. No OPA. Just write what you want enforced: “All S3 buckets must have server-side encryption enabled” or “No EC2 instances larger than m5.xlarge in staging,” and Terracotta AI automatically evaluates every PR against your policies.
The Guardrail Report shows a pass/fail result for each active policy, with clear explanations for any violations. Guardrails can run in advisory mode (flag but don’t block) or mandatory mode (block the merge until the violation is resolved).
This is policy-as-code without the code. Your compliance team defines the rules. Your engineers see them enforced in real time. Nobody has to learn a new language.
Terraform PR Conflict Report
Infrastructure PRs don’t exist in isolation. When two engineers work on overlapping resources in separate PRs, the second to merge can silently break the first one’s assumptions.
The PR Conflict Report identifies potential conflicts between the current PR and other open PRs targeting the same resources or state. This is the kind of issue that causes production incidents on Friday afternoons, and it’s completely invisible in a normal code review workflow.
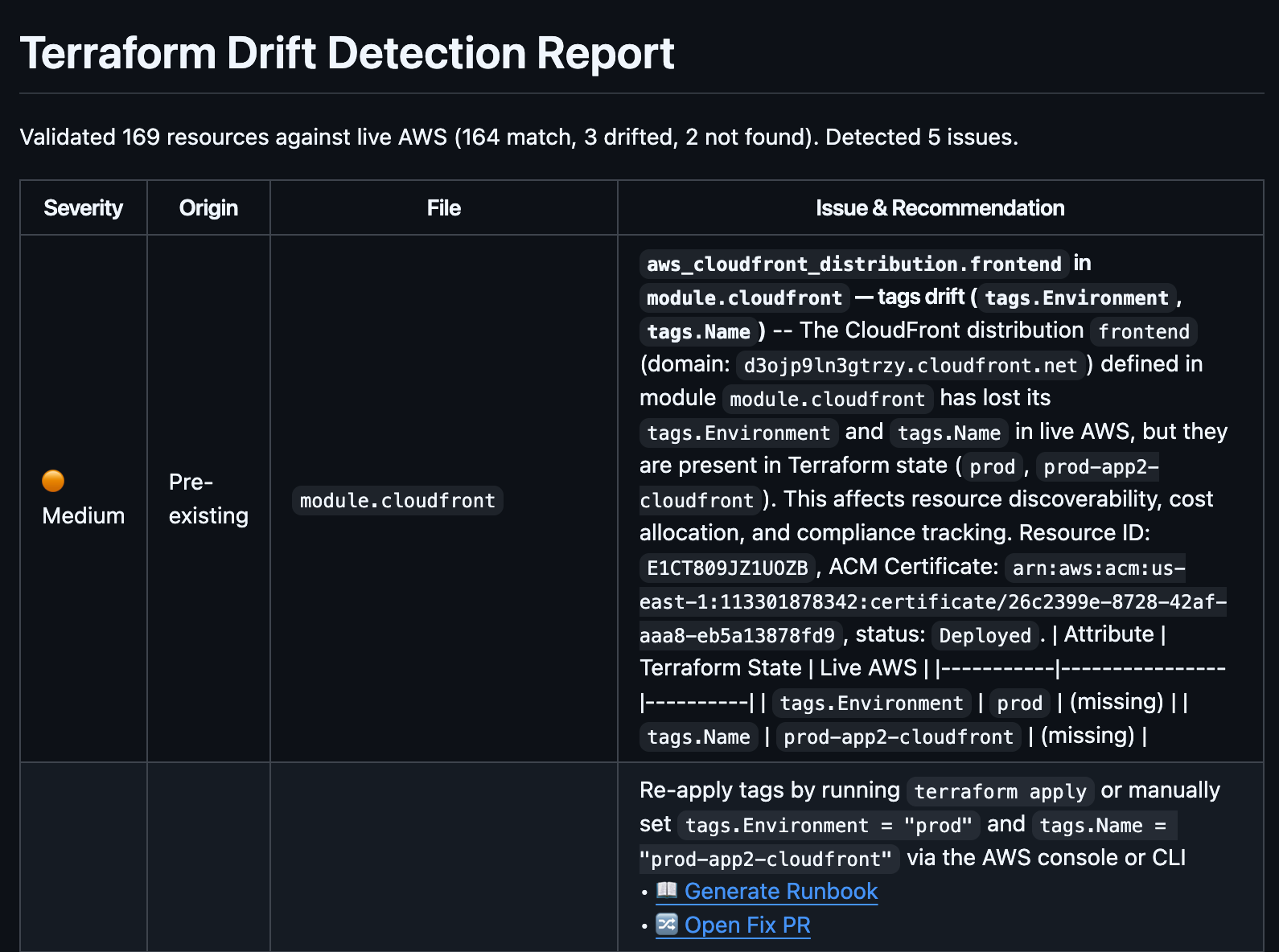
Terraform Drift Detection Report
This is the section that makes infrastructure engineers sit up in their chairs.
Drift happens. Someone makes a manual change in the console. An automated process modifies a resource outside of Terraform. A previous apply partially failed, leaving the state inconsistent. Whatever the cause, your Terraform code no longer matches reality, and your next apply is about to do something you didn’t expect.
Terracotta AI’s drift detection compares your PR against your actual remote state and live infrastructure across 1,618 AWS resource types. It performs field-level comparison, so you don’t just know that a resource has drifted, you know exactly which attributes changed, what the expected value was, and what the current value is.
The Drift Detection Report shows each drifted resource with detailed findings, severity levels, and context for how the drift affects the changes in this PR. If your PR is about to modify a resource that has already drifted, you need to know that before you hit apply, not after.
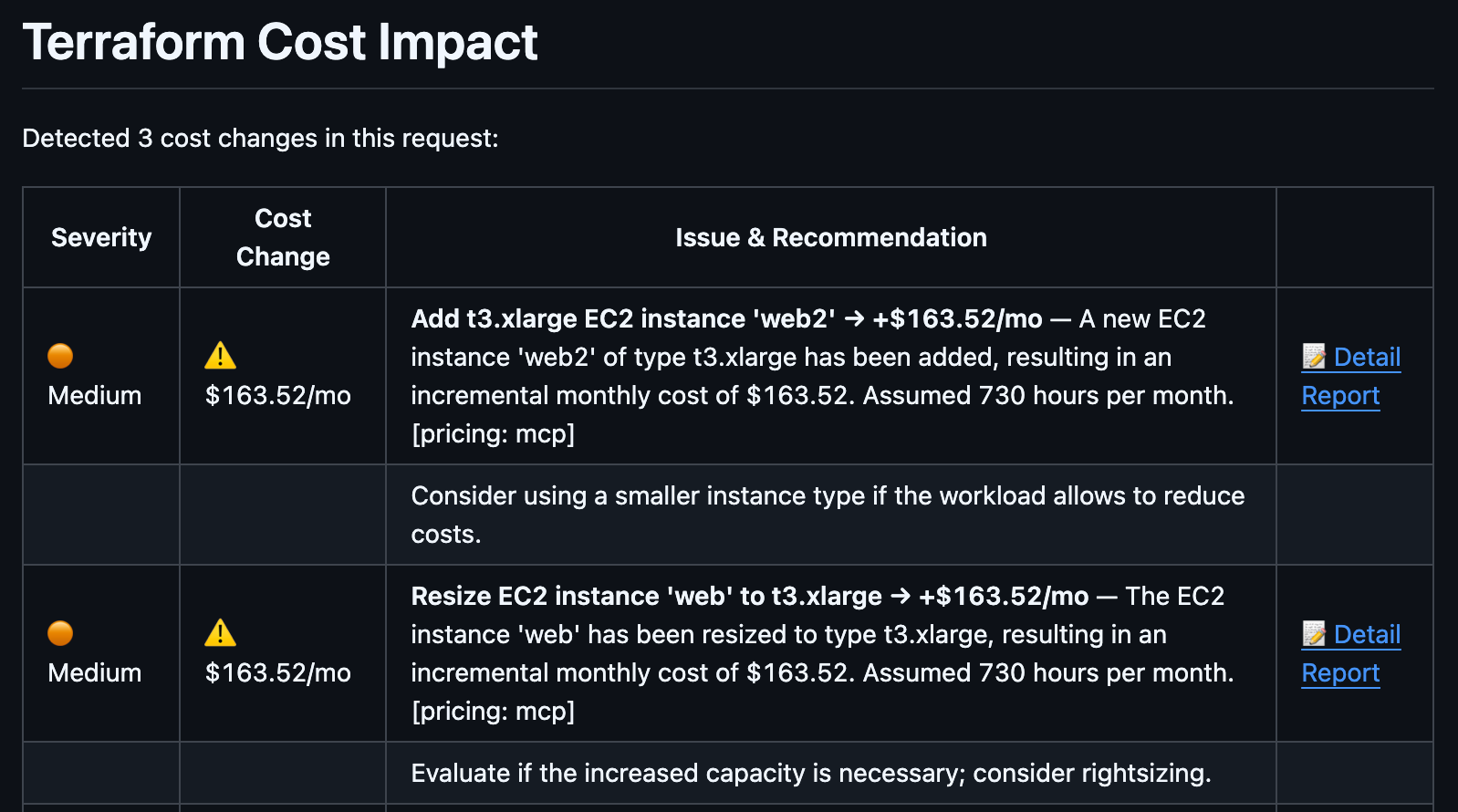
Terraform Cost Impact
Every Terraform change has a cost implication. Adding a new RDS instance, resizing an EC2 fleet, and enabling a new service all show up on next month’s bill, and the engineer writing the code often has no idea what the number looks like.
The Cost Impact section breaks down the estimated monthly cost delta of the changes in this PR. It shows per-resource cost estimates so your team can see exactly which resources are driving the number. No more surprise bills. No more “who approved that m5.4xlarge?”
This is the conversation your FinOps team has been trying to have with engineering for years. Terracotta AI puts the number in front of the engineer at the exact moment it matters before they merge.
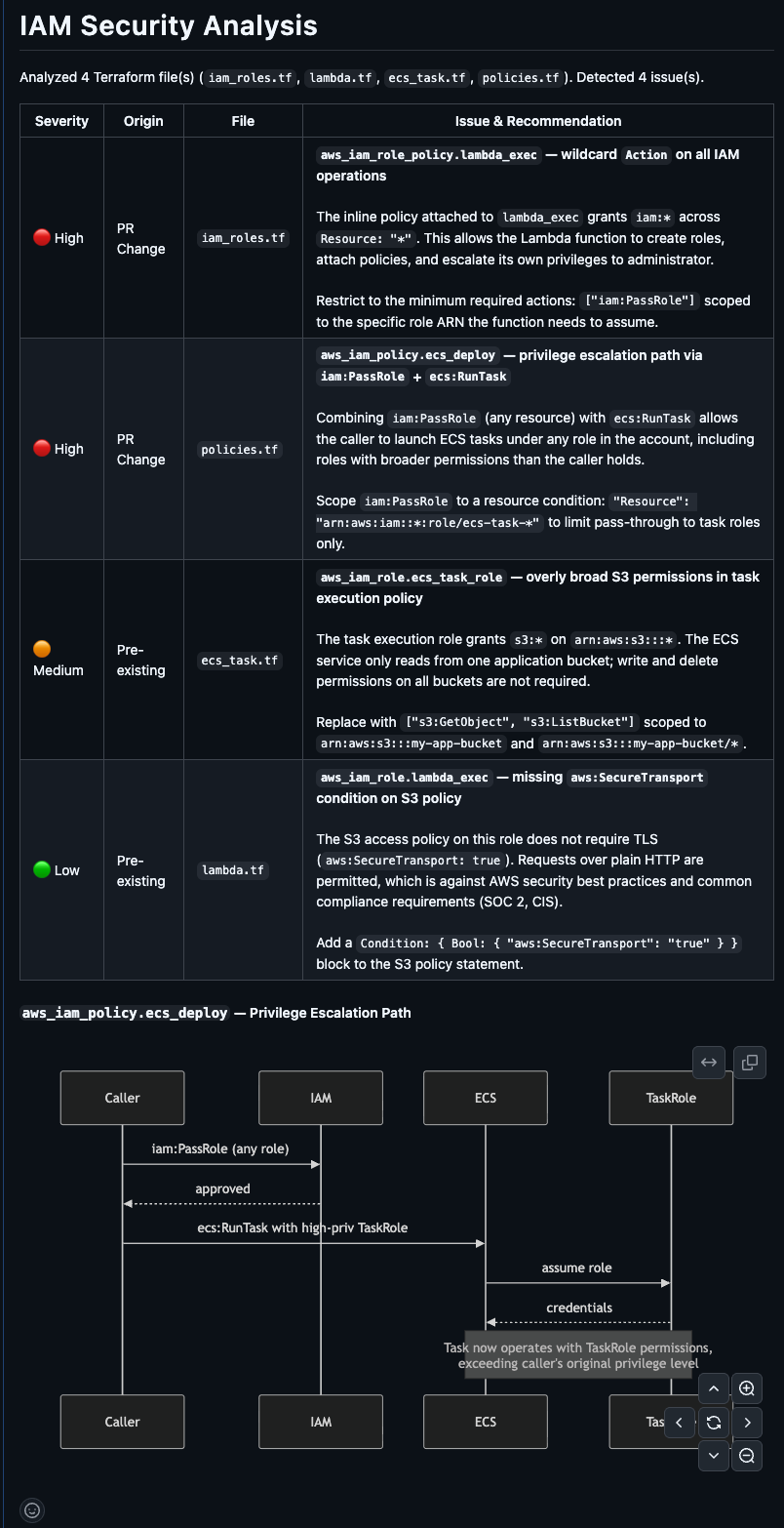
IAM Security Analysis
IAM misconfigurations are the number one cause of cloud security breaches, and they’re the hardest thing to catch in a code review. An overly permissive policy, a wildcard action, and a missing condition key look fine in a diff but create real exposure in production.
The IAM Security Analysis evaluates every IAM-related change in the PR against security best practices. It flags overly broad permissions, missing least-privilege constraints, and risky policy patterns with clear explanations of why each finding matters and how to fix it.
For regulated industries, healthcare, financial services, and government, this section alone can justify the tool.
Tag Compliance Check
Tags are the foundation of cloud cost allocation, access control, and compliance reporting. And they’re the first thing engineers forget when they’re shipping fast.
The Tag Compliance Check validates that every resource in the PR meets your organization’s tagging requirements. Missing tags, incorrect formats, and inconsistent naming all caught before merge, not after your FinOps team sends the quarterly “please tag your resources” email.
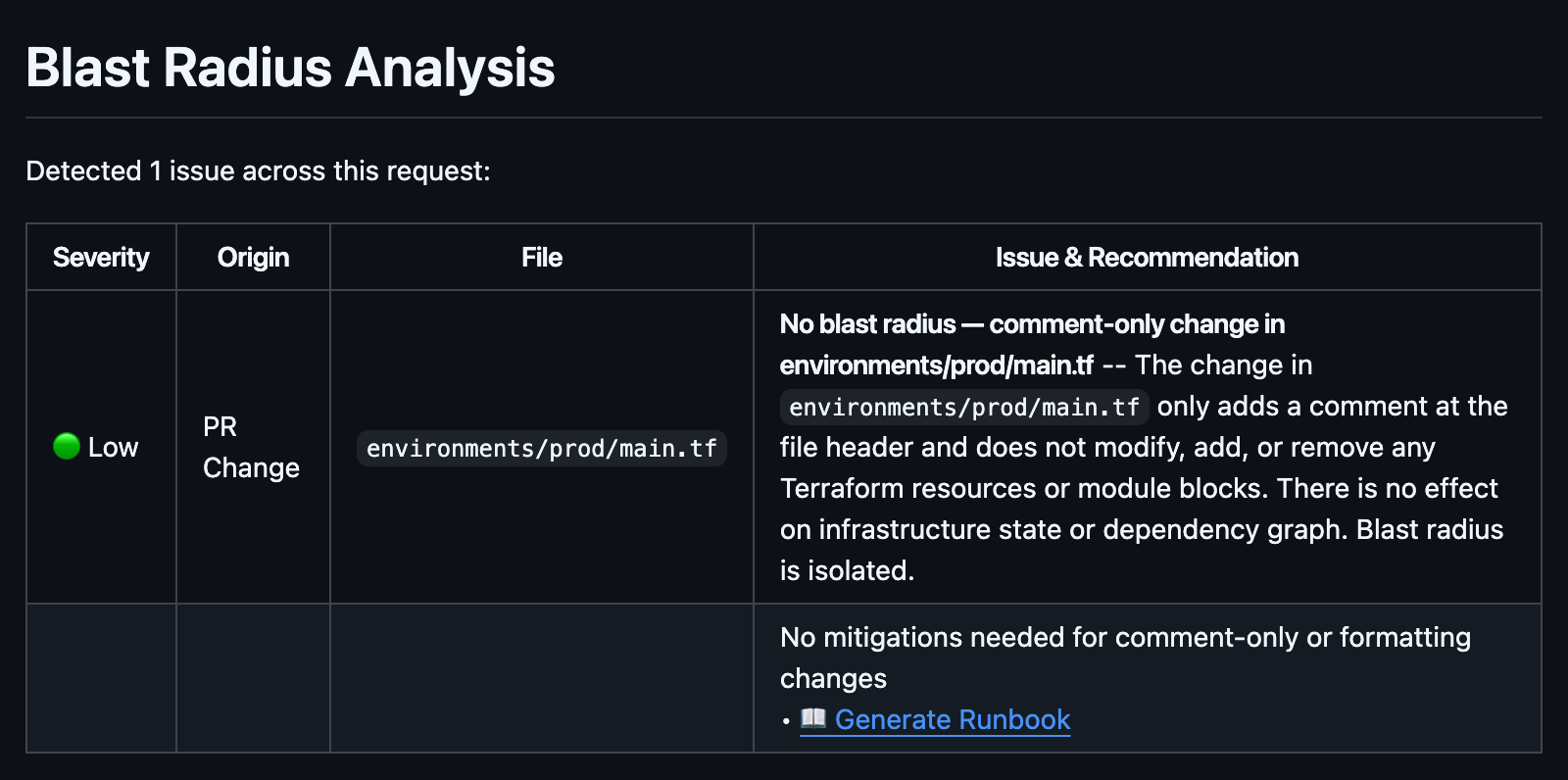
Blast Radius Analysis
Not all Terraform changes are created equal. Modifying a single security group rule is not the same as replacing a VPC. But in a raw plan output, they can look equally mundane.
The Blast Radius Analysis evaluates the scope and severity of changes in the PR, the number of resources affected, which dependencies could be affected, and the potential downstream consequences. It provides a severity rating and a table breaking down the impact by resource.
This is the analysis a senior infrastructure engineer runs through in their head when reviewing a plan. Terracotta AI does it automatically, consistently, and documents it for every PR.
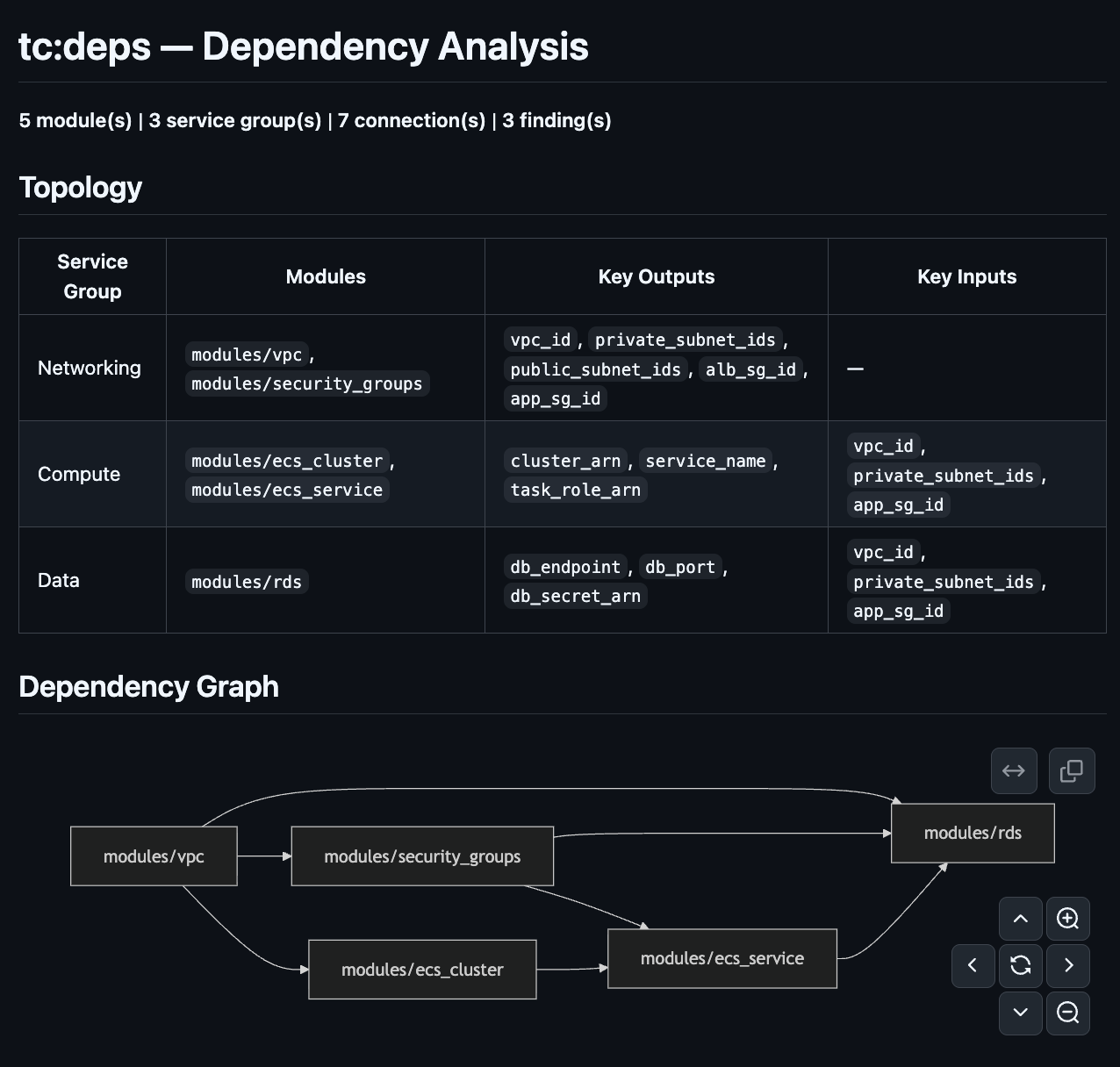
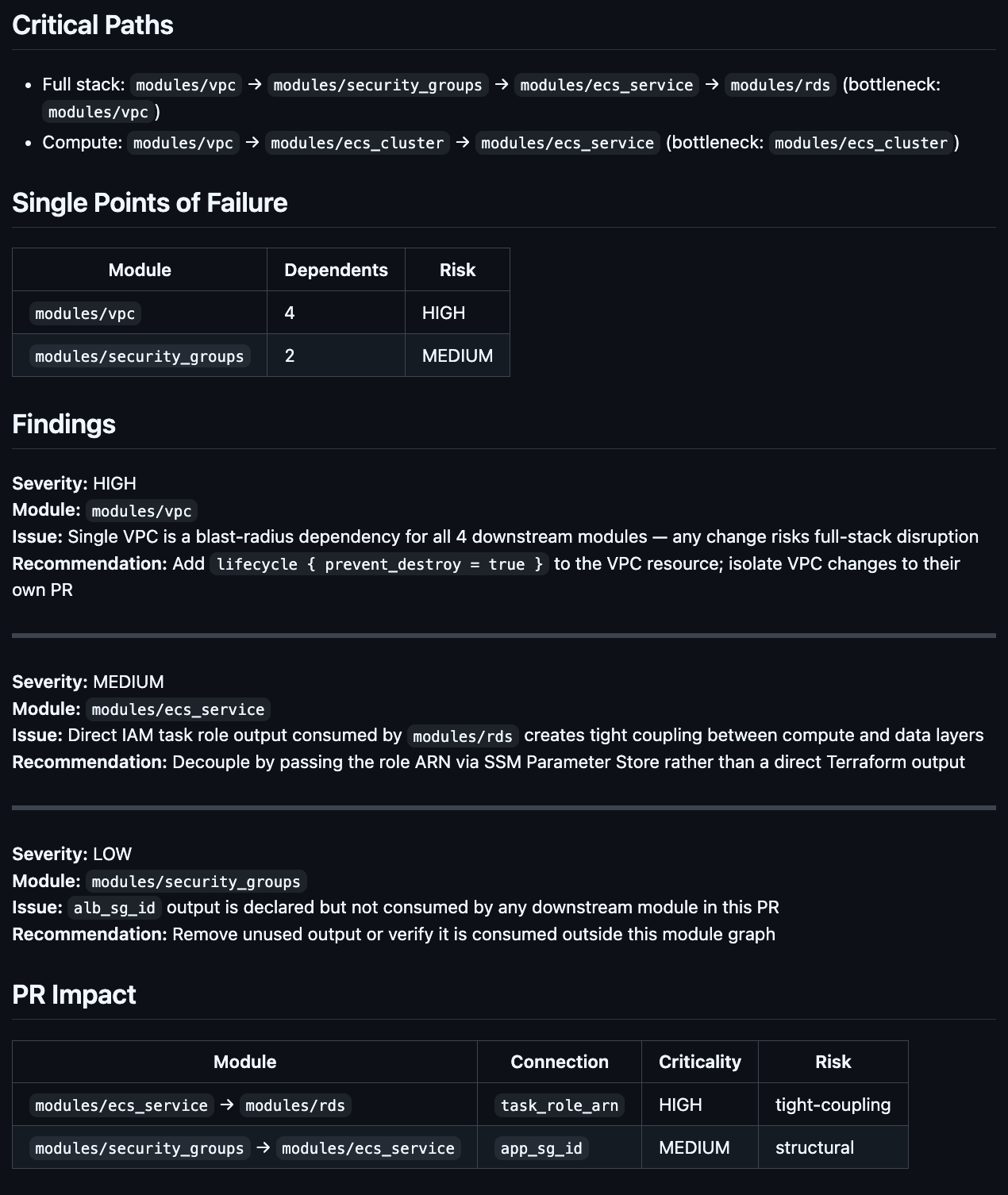
Infrastructure Dependencies
Understanding what depends on what is the difference between a safe deployment and an outage. The Infrastructure Dependencies section maps the dependency graph of the resources in your PR, showing which resources reference other resources, which modules depend on which outputs, and where a single change could cascade.
This is the context that’s impossible to see in a flat diff. A security group change might look harmless until you realize four auto scaling groups and a load balancer depend on it. The dependency map makes that visible before anyone hits approve.
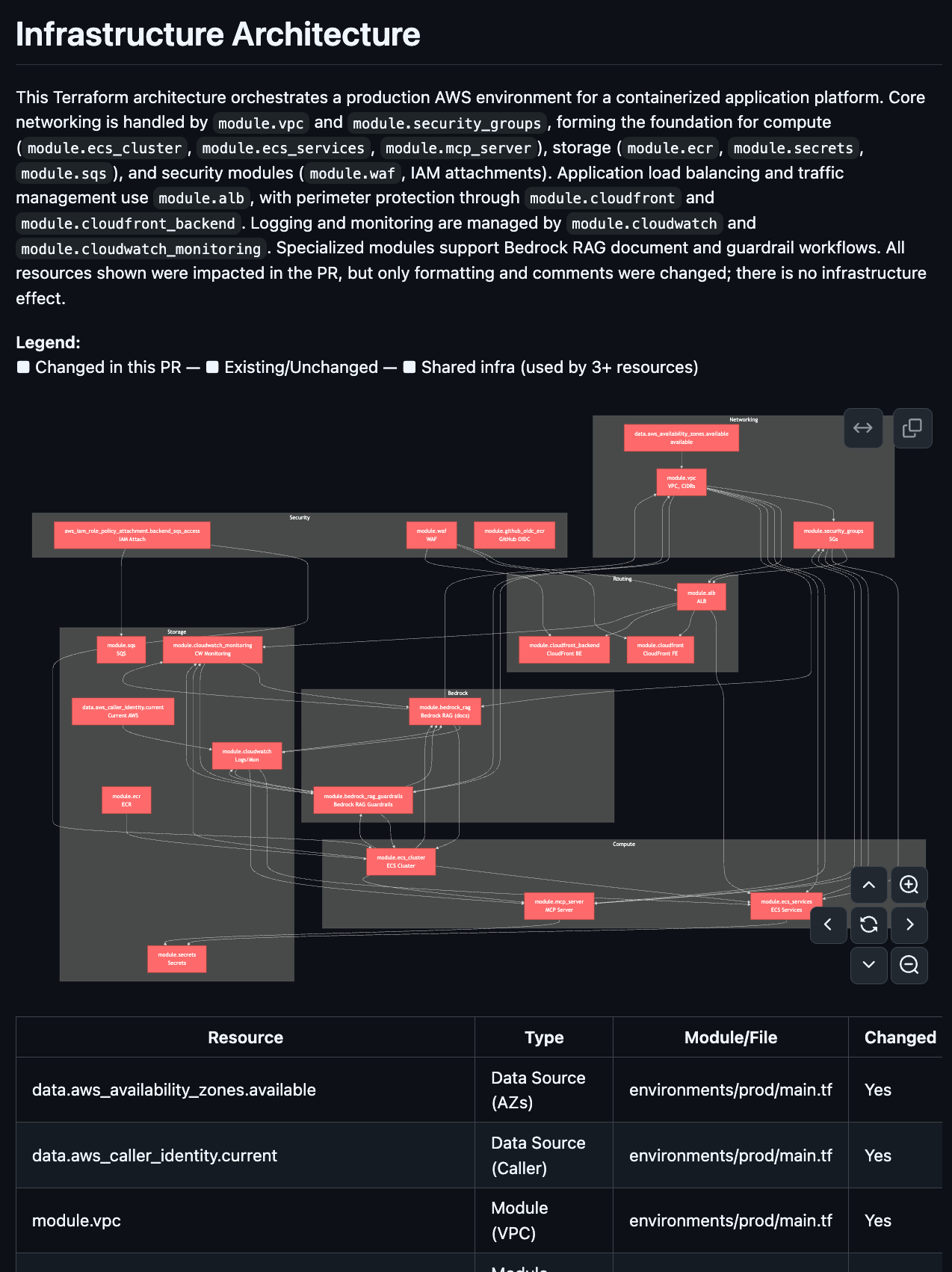
Infrastructure Architecture Diagram
This is the feature that makes people stop scrolling.
Terracotta AI generates a Mermaid architecture diagram directly in the PR comment, showing how the resources in this PR relate to each other and to the broader infrastructure. You can view the VPC, subnets, security groups, instances, and load balancers as a visual diagram directly in GitHub or GitLab.
For complex PRs touching multiple resources, this is the fastest way to understand what’s actually changing. No more mentally reconstructing the architecture from a list of resource addresses. The diagram shows you.
What This Means for Your Team
Every section above runs automatically on every PR. There’s nothing to configure beyond connecting your repo: no scripts to maintain, no policy languages to learn, no pipeline changes to make.
Your platform engineers will no longer be the bottleneck. Your junior engineers get senior-level feedback on every change, while your security team gets visibility without slowing anyone down. Your FinOps team stops finding surprises in the monthly bill. And your compliance team gets enforcement without writing a line of Rego.
This is what an AI-powered infrastructure review actually looks like, not a chatbot that guesses at your code, but a system that understands your live infrastructure, your remote state, your drift, your policies, your architecture, your code, and your proposed changes. This gives your team the context they need to ship faster and with confidence.
Your team deserves better than rubber-stamped plans.
Ready to See It on Your Infrastructure?
Terracotta AI is built for platform engineering teams managing Terraform at scale. We're SOC 2 Type II certified, HIPAA compliant, and currently running with teams in healthcare, financial services, and insurance.
Terracotta AI is agnostic to your IaC tooling and can integrate with GitHub, GitLab, HCP Terraform Run Tasks, and many other tools - no pipeline changes, no new workflows to learn.
Interested in a technical demo?




Comments ()