"Looking Back, We Should've Caught It"

There's a moment that sticks with every DevOps engineer:
The PR looked clean. The plan showed no red flags. Everyone approved. And then — the incident. A public bucket. An over-permissioned IAM role. An unencrypted volume. "How did this get through?" someone asks. But the better question is: "How were we supposed to catch it?"
Most security issues in Terraform don't announce themselves with alarms — they drift quietly, hidden in defaults, manual hotfixes, or missed context. And by the time they show up in production, it's already too late.

The Data Doesn’t Lie: Terraform Misconfigurations Are Everywhere
Let’s zoom out momentarily and look at the broader picture, because the numbers speak volumes.
Over 50% of Terraform modules contain security misconfigurations. A study by Bridgecrew (now part of Prisma Cloud) found that more than half of the Terraform modules analyzed in open-source repositories had at least one security misconfiguration. These included:
- Publicly accessible S3 buckets
- Security groups with open ingress (0.0.0.0/0)
- IAM policies with wildcard actions
These aren’t theoretical concerns. They are real-world vulnerabilities that appear in the majority of Terraform codebases, and they can lead to privilege escalation, lateral movement, and data leaks.
Misconfigurations account for 95% of cloud security failures. According to Gartner, by 2025, 99% of all cloud security failures will be caused by customer misconfiguration, not flaws in the cloud providers themselves. That includes infrastructure defined in Terraform. This means the burden of secure infrastructure doesn’t rest on AWS or GCP; it rests on us.
44% of IaC scans surface high or critical vulnerabilities. Snyk’s 2023 report found that nearly half of all infrastructure-as-code scans flagged high or critical vulnerabilities. These ranged from hardcoded secrets to overly permissive IAM roles to vulnerable container images. These aren’t edge cases — they’re familiar.
This is the scale of the problem we’re dealing with. That’s why security in Terraform needs to be proactive, contextual, and embedded in the way we build and review infrastructure.
Terraform Security Today: Invisible, Until It Isn't
Terraform is powerful. But with that power comes risk, and not just in theory. In practice:
- A missing versioning block on an S3 bucket leaves it unrecoverable.
- A default IAM role allows wildcard permissions.
- A "small" module update wipes a security group tied to multiple services.
These aren't rare edge cases. They happen because security in Terraform is often:
- Decentralized
- Hidden behind layers of abstraction
- Assumed to be someone else's problem
We've seen teams implement policy-as-code, enforce plan checks, and standardize modules. These are good steps, but the truth is, they aren't enough.
Problem: Security Isn't Embedded in the Review
Security issues don't get missed because engineers are careless. They get missed because they don't show up where decisions are made.
Today's workflows:
- Run policies after the plan
- Gate merges with basic validations
- Assume reviewers will "know better"
But that's not realistic.
Reviewers are tired. Teams are shipping fast. The Terraform plan doesn't tell you why something is happening. And security policies — when they exist — often live outside the PR in a CI log, a dashboard, or a Slack notification that gets missed.
This creates a disconnect: the change is reviewed without the full picture, and the risk is discovered after it's too late.
A Better Way: AI That Understands Terraform Security
One question we hear a lot:
"Why not just paste the Terraform into ChatGPT or Claude?"
The answer is simple: general-purpose LLMs don't know your infrastructure. They don't see your state file. They don't understand drift. They don't know what your team fixed manually during a 2 a.m. incident or what policies you've silently enforced through module conventions.
At best, they give you a generic explanation. At worst, they confidently miss the nuance that makes infrastructure risky in the first place. This isn't a documentation lookup problem. It's a context problem.
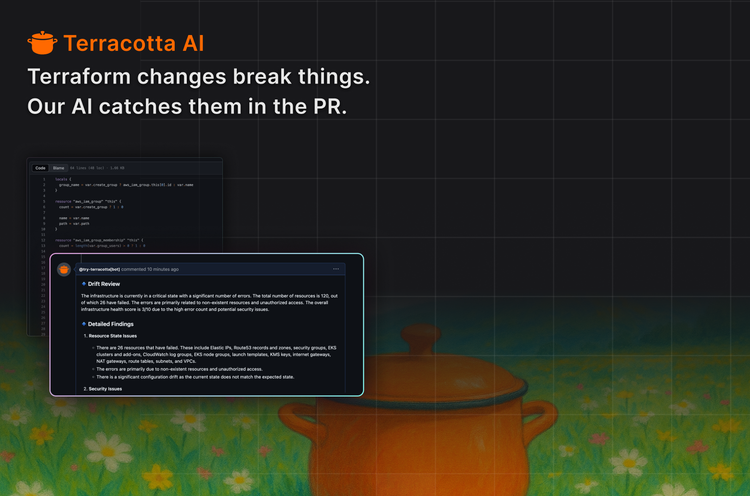
That's exactly why we built Terracotta AI—not just to "understand Terraform," but to understand your Terraform in the context of your cloud, your state, your team, and your change history. Copy-pasting code into a chat window won't tell you that your plan is about to undo a production hotfix. Terracotta AI will.
Here's how we do it:
At Terracotta AI, we believe the right place to catch Terraform security risks isn't after deployment — it's in the PR, when the change is being reviewed.
We've built a system that brings security context directly into the workflow:
- State-aware analysis: We pull in Terraform state and live cloud metadata to detect when your PR reverts a hotfix or introduces exposure.
- Inline security alerts: Terracotta AI flags risky changes right in the diff, with natural-language explanations of why something is dangerous.
- Drift-informed decisions: We tell you when the plan looks clean, but drifted infrastructure is about to be affected.
- Policy context, not just enforcement: Instead of "this fails policy," we surface policy impact in a human-readable format — empowering reviewers instead of blocking them.
And all of this happens inside GitHub or GitLab, where infrastructure decisions are actually made.
This Isn't Just About Security — It's About Trust
Security breakdowns don't just hurt systems — they hurt collaboration.
- Devs lose trust in the platform team.
- Ops get stuck in fire-fighting mode.
- Reviews become gatekeeping instead of guidance.
By embedding AI directly into the review process, Terracotta AI gives both sides what they need:
- Developers get clarity and speed.
- Platform teams get visibility and guardrails.
No more guessing. No more surprises. Just safer Terraform changes, reviewed with an accurate understanding.
A New Model for Securing Infrastructure
Infrastructure is moving too fast for security to be bolted on.
We believe it needs to be:
- Contextual
- Continuous
- Embedded in the workflow
Terracotta AI isn't a scanner, not just another policy engine. It's an AI assistant that thinks like a senior security-aware infrastructure engineer and appears in every PR. Because looking back and saying, "We should've caught it," isn't good enough. We'd rather say: "We caught it. And we fixed it before it shipped."
Want to review Terraform with security in mind — without slowing down your team? 👉 Try Terracotta AI.



Comments ()