Enforcing Sentinel Policies Earlier in Your GitOps Pipeline: Migrating Sentinel Policies to AI Guardrails in Under 5 Minutes
TL;DR:
HashiCorp’s Sentinel is robust but often reactive, enforcing policies only after Terraform plans run. Terracotta AI complements it by bringing those same Sentinel policies into the workflow earlier. In minutes, teams can translate Sentinel rules into natural-language guardrails that run directly in pull requests, giving developers instant, human-readable feedback before CI/CD.
Together, Sentinel and Terracotta create a full-stack governance model: Sentinel remains the enforcement engine in Terraform Cloud, while Terracotta serves as the pre-merge safety layer, catching risks, drift, and policy violations before they ever reach a plan.
Terraform policy enforcement has always walked a fine line, balancing safety with speed. HashiCorp's Sentinel framework was a significant leap forward, giving platform teams a powerful way to codify security, compliance, and cost controls directly into Terraform runs. Sentinel turned governance into code precise, testable, and repeatable. But like any powerful system, it requires expertise and ongoing maintenance to get right. As HashiCorp's actual footprints, teams, and repositories grow, so does the friction of managing and scaling those policies consistently across every workspace.
Terracotta AI builds on that foundation. Rather than replacing Sentinel, it brings the same guardrails into the workflow earlier, acting as an intelligent, pre-merge complement that translates Sentinel logic into natural-language guardrails developers actually understand. In under five minutes, teams can sync existing Sentinel policies with Terracotta AI and start running the same enforcement checks directly inside pull requests, long before Terraform Cloud or Enterprise runs the plan. The result is a faster feedback loop, more transparent communication between developers and platform teams, and fewer policy violations reaching CI/CD.
What Sentinel Policies Are (and Why They Matter)
Sentinel is HashiCorp's policy-as-code framework for Terraform Cloud and Enterprise. It lets teams define governance logic programmatically, things like enforcing encryption on S3 buckets, restricting instance types by environment, or ensuring tagging compliance across resources. Each policy is written in Sentinel's domain-specific language (DSL) and in HashiCorp's Terraform plan data, and it lets platform teams enforce organizational standards in a controlled, versioned way.
A typical Sentinel policy might look like this:
Import "tfplan/v2" as tfplan
main = rule {
all tfplan.resources.aws_s3_bucket as bucket {
bucket.applied.acl not in Sentinel sead", "public-read-write"]
}
}It’s a powerful model, but it’s also a precise one, which means teams need to understand Terraform plan schemas, maintain imports across provider versions, and manage policies as infrastructure evolves. Sentinel enforces control during plan evaluation, giving teams confidence that nothing unsafe reaches deployment.
The Practical Challenges: Feedback Comes Late.
It's Sentinel's greatest strength, precise enforcement within Terraform Cloud, which also introduces friction when teams move fast. Because Sentinel policies run during or after plan execution, developers often don't see violations until late in the process. By the time a "policy check failed" message appears, they've already opened, pushed, and sent to Sentinel's pipeline. That delay creates a gap between the writing infrastructure and understanding what's wrong with it.
It's not a flaw in Sentinel; it's a timing issue. The model was built for central teams that don't manage Terraform runs, but today's teams operate across "multiple repos, branches, and CI/CD systems. Governance that lives exclusively inside the plan stage can feel disconnected from where collaboration happens: inside pull requests. Platform teams. It's a way to bring Sentinel's governance philosophy closer to where developers work earlier in the feedback loop, with the same enforcement logic but better visibility.
Terracotta AI: Policy Awareness Before the Plan
That's precisely where Terracotta AI fits. Terracotta AI brings Sentinel-style governance into the pull request itself, running pre-merge checks, translating Sentinel rules into plain language, and providing actionable context. It connects directly to GitHub or GitLab and automatically scans every Terraform and CDKTF PR before merge, surfacing cost-impact detection and policy violations, all explained in English, not just DSL output.
For example, a Sentinel rule that blocks public S3 buckets translates in TerracottaAI to:
"Block any Terraform change that makes an S3 bucket publicly accessible."
Or a cost policy like restricting small EC2 instance types becomes:
"Flag any EC2 instance smaller than t3.small in production."
The intent stays the same, the enforcement moves earlier, saving time. Developers can see violations before Terraform Cloud runs a plan. Platform leads can track adherence across all repositories. Sentinel continues enforcing compliance during plan and application, but "now the team sees and understands issues long before that stage.
Working Hand-in-Hand With Sentinel
The point of Terracotta AI isn't to replace Sentinel, it's to extend it. Sentinel remains the definitive enforcement layer inside Terraform Cloud and Enterprise, where actual plan data is validated and blocked if needed. Terracotta AI complements that by acting as a sanity check and collaboration layer at the PR level. It catches potential issues earlier, provides context for developers, and helps teams align on policy intent before the pipeline even starts.
The benefits compound at scale. Platform teams no longer spend cycles explaining Sentinel failures after the fact. Developers no longer have to reverse-engineer policy DSL. Everyone gets faster, more precise feedback, without compromising governance.
And since Terracotta AI supports natural language guardrails, teams can layer in additional pre-merge checks that cover contextual risks Sentinel wasn't designed to handle, such as cost visibility, dependency risk, and drift detection across multiple repos.
Migrating Sentinel Policies to Terracotta AI (in Under 5 Minutes)
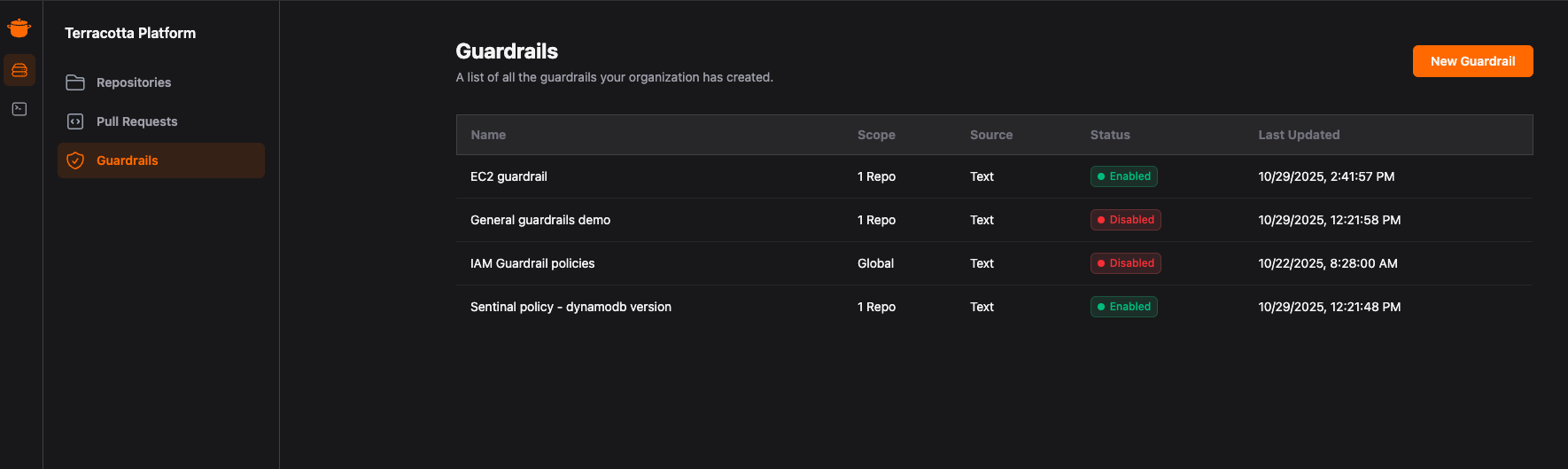
Step 1: Open up the Guardrails section in the Terracotta AI app and create a new Guardrail:
Step 2: Give the Guardrail a Name and copy and paste your Sentinel Policies into the Context section.
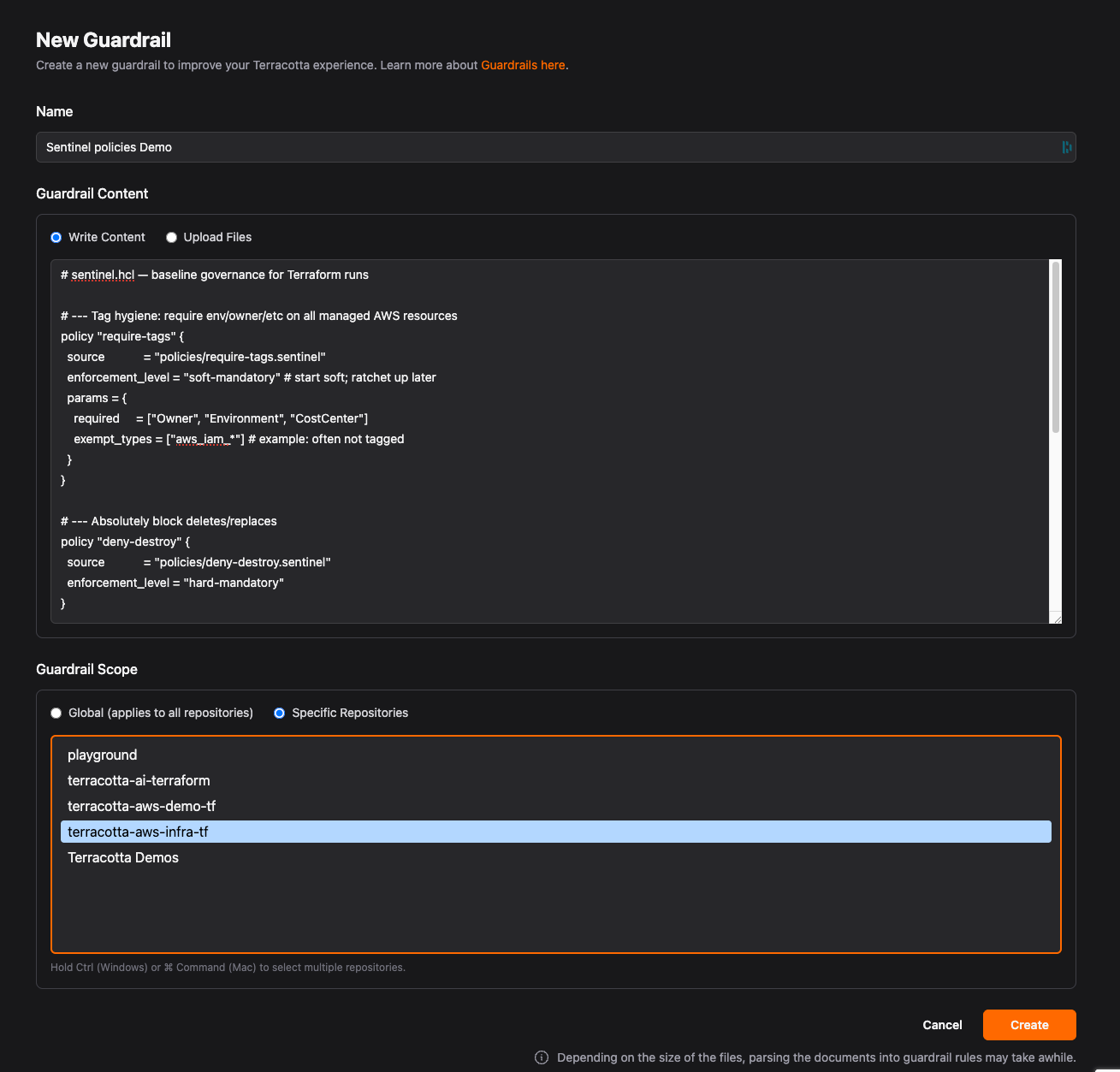
Here is the example Sentinel Policy the Context area we are using:
# sentinel.hcl — baseline governance for Terraform runs
# --- Tag hygiene: require env/owner/etc on all managed AWS resources
policy "require-tags" {
source = "policies/require-tags.sentinel"
enforcement_level = "soft-mandatory" # start soft; ratchet up later
params = {
required = ["Owner", "Environment", "CostCenter"]
exempt_types = ["aws_iam_*"] # example: often not tagged
}
}
# --- Absolutely block deletes/replaces
policy "deny-destroy" {
source = "policies/deny-destroy.sentinel"
enforcement_level = "hard-mandatory"
}
# --- Cap proposed monthly cost using HCP/TFE cost estimates
policy "limit-monthly-cost" {
source = "policies/limit-monthly-cost.sentinel"
enforcement_level = "hard-mandatory"
params = {
max_monthly = 1000.00
}
}
# --- Allowed AWS regions only (guardrails for drift/accidental regions)
policy "allowed-aws-regions" {
source = "policies/allowed-aws-regions.sentinel"
enforcement_level = "soft-mandatory"
params = {
regions = ["us-east-1", "us-west-2"]
}
}When you click create , we will begin parsing and contextualizing the Sentinel Policy into enforcement rules.
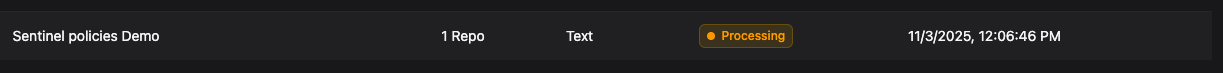
Step 3: You are done. Yes, that's it. We will parse the Sentinel rules and enforce them when a Terraform PR is created. You can apply these at a Global or Repo level.
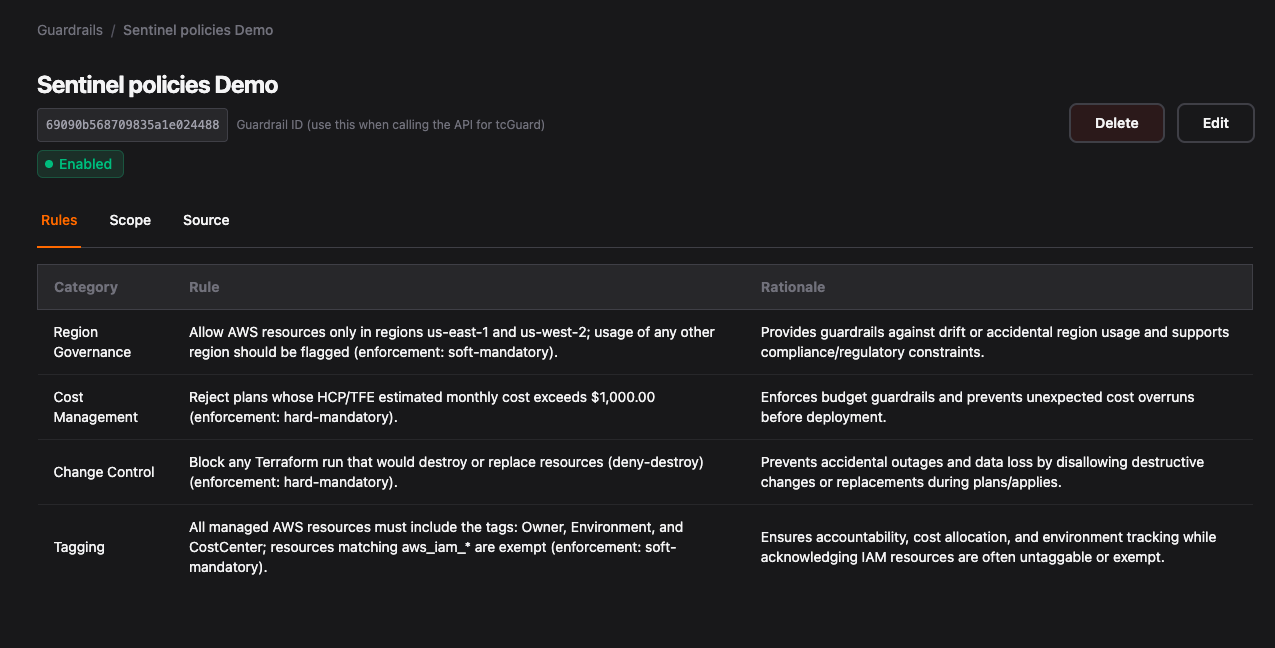
Step 4: Open a repo and see Terracotta AI Guardrails in action, enforcing your Sentinel policies pre-code merge!
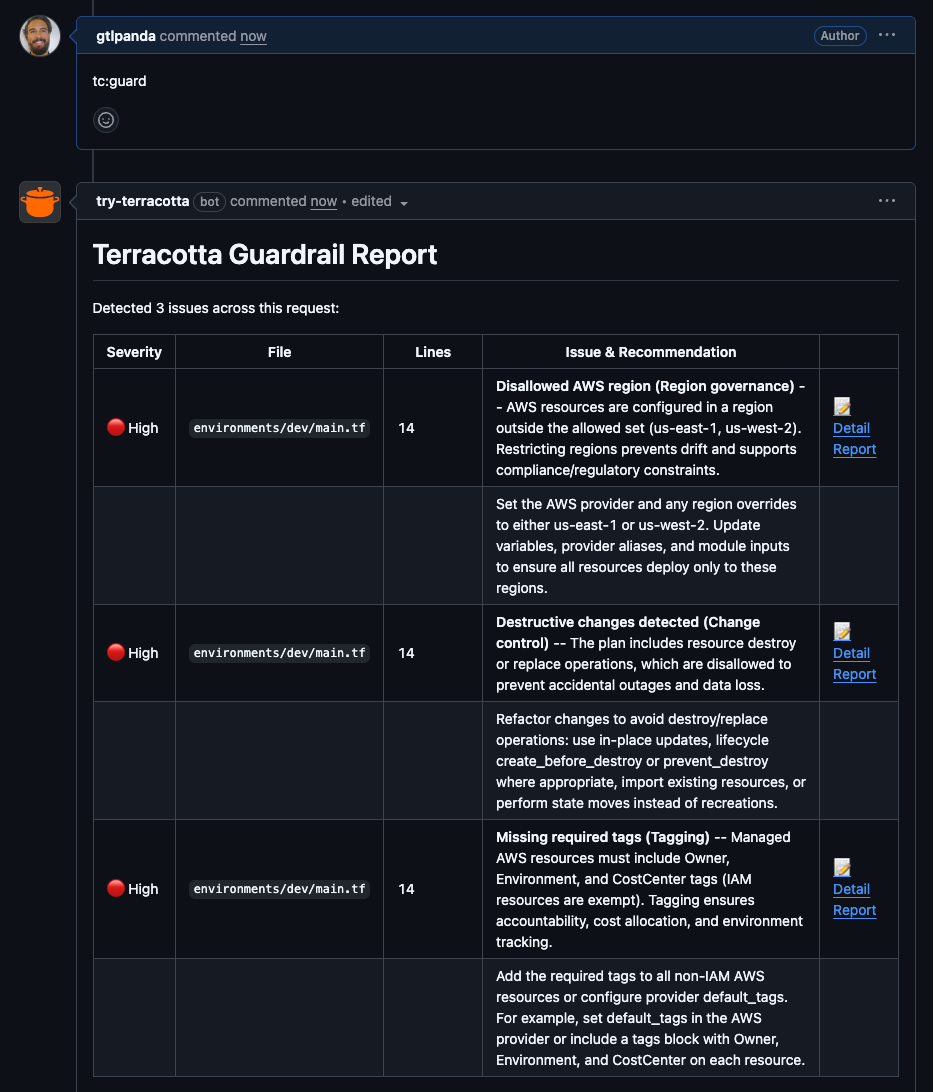
From Policy-as-Code to Policy-as-Intent
The evolution isn't about choosing one over the other; it's about combining both. Sentinel gives platform teams precision and enforcement at the plan stage. Terracotta AI gives them clarity and context earlier in the workflow. Together, they turn policy-as-code into policy-as-intent: consistent governance, understood by both developers and platform engineers, is applied from the first commit to final deployment.
When a Terracotta AI guardrail flags an issue, it doesn't just say a rule failed; it explains the "why":
"EC2 instance t2.micro exceeds your production performance baseline. Replace with t3.small or larger."
That level of transparency makes compliance conversational, not combative. Developers learn as they go. Platform teams enforce standards proactively. Sentinel remains the final Terracotta AI to ensure fewer violations ever.
Final Thoughts
HashiCorp set the standard for infrastructure governance with Sentinel. Terracotta AI builds on that foundation, extending its reach to where developers actually collaborate, and translating its rules into a context everyone can understand. The two systems are complementary: Sentinel enforces; Terracotta AI informs. Together, they bring the same rigor and consistency HashiCorp pioneered, but with the speed, clarity, and AI assistance modern platform teams need.
Governance doesn't have to slow you down. It just needs to meet you where you work. Terracotta AI brings Sentinel's power earlier in the lifecycle, keeping infrastructure compliant, auditable, and understandable at every step.
Try Terracotta AI for free and bring your Sentinel policies into every PR in under five minutes.
Interested in a demo of Terracotta AI? Sign up at https://tryterracotta.com/schedule-demo and we'll create a custom demo for you


Comments ()