Terraform Drift Detection: Causes, Prevention, and Safe Remediation

TL;DR:
- Terraform drift occurs when the actual infrastructure differs from your code and state, often due to manual changes, automation tools, or provider updates.
- Terraform drift causes risky, confusing plans and broken deployments. Traditional drift detection is manual, noisy, and reactive.
- Terracotta AI shifts drift detection left by using natural language IaC AI Guardrails to analyze your code, diff, pipeline, and live infrastructure in pull requests, flagging and explaining drift before it reaches CI/CD so you can remediate safely, enforce policies, and ship with confidence.
Terraform drift sneaks in quietly and turns "source of truth" into "source of surprise." You ship clean plans, and weeks later, production no longer matches your .tf or state. Now every plan feels suspicious, and applying feels risky.
This guide goes deep on what drift is, why it happens, how to detect and remediate it safely, and how Terracotta AI automates drift detection directly in pull requests before risky changes ever reach CI/CD.
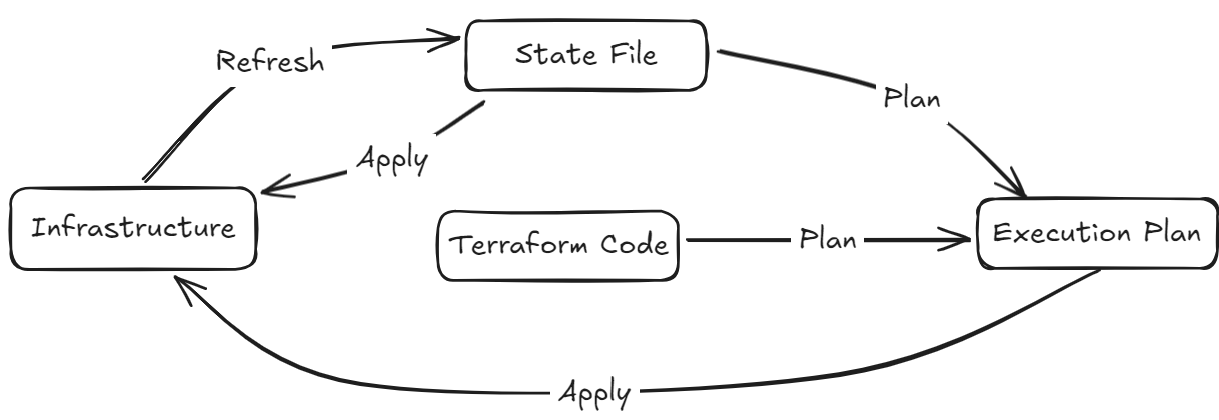
What is Terraform drift?
Terraform drift occurs when the real infrastructure in your cloud environment no longer matches the configuration stored in Terraform state and code.
In simpler terms, something changed outside of Terraform's control.
That could mean:
- A developer made an S3 bucket public in the AWS console.
- A database instance was resized manually.
- Another automation tool modified a Terraform-managed resource.
- Or a cloud provider silently changed a default setting.
Once that happens, Terraform is no longer operating from a reliable truth.
The next plan output becomes confusing or even destructive because it's trying to reconcile the wrong baseline.
Common causes of drift
- Manual console or CLI changes
The most common cause.
Someone fixes a production issue in the console, bypassing IaC entirely. The hotfix might work in production, but Terraform's state is now outdated.
- External automation
Drift also occurs when other tools, such as Ansible, Helm, or CloudFormation, modify resources that Terraform also manages.
Each system assumes ownership, and Terraform can't see what changed.
- Lifecycle configuration masking
Using ignore_changes in Terraform can suppress legitimate drift:
lifecycle {
ignore_changes = [tags]
}That setting hides tag updates from future plans. It's useful for noise, but dangerous for compliance-related metadata.
- Provider or API updates
Cloud providers constantly evolve APIs. Defaults shift. New fields appear.
A field Terraform once ignored can suddenly appear in drift results or worse, silently mutate infrastructure behavior.
- State file desynchronization
If multiple users or pipelines apply changes without proper state locking, you end up with competing state updates.
One overwrites another, and Terraform's record diverges from the actual environment.
How Terraform detects and misses drift
When you run terraform plan, it compares three things:
1. The desired configuration (your .tf files)
2. The state file (the recorded infrastructure snapshot)
3. The real-world resources (fetched from the provider API)
If something differs, Terraform flags it. But this process is reactive; you must run the command to detect drift.
Terraform detects manual console changes, missing resources, or modified attributes that are modeled in the provider schema.
It misses untracked fields, ignores attributes, and doesn't track mutations made by tools Terraform doesn't manage.
That means drift can persist for weeks without notice until the next plan or failed deployment exposes it.
Prevention strategies
- Lock and centralize your state
Use remote backends like S3, GCS, or Terraform Cloud with locking enabled to prevent concurrent state writes.
Example for AWS:
terraform {
backend "s3" {
bucket = "iac-state-prod"
key = "networking/terraform.tfstate"
region = "us-east-1"
dynamodb_table = "iac-state-locks"
encrypt = true
}
}- Restrict manual cloud access
Lock down console and CLI write access.
Emergency fixes should follow a break-glass policy and must be reconciled back into Terraform code immediately.
- Minimize ignore_changes
Audit your lifecycle rules regularly.
Only ignore attributes that truly change outside your control, such as timestamps or ephemeral metadata.
- Keep providers updated
Provider updates often resolve drift-detection issues and schema mismatches.
Pin and upgrade versions consistently:
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 5.59"
}
}
}- Detect drift proactively
Schedule drift-detection jobs, or, better yet, integrate them directly into your pull request reviews. Catching drift before the merge keeps every change based on live, accurate infrastructure.
Detecting drift: practical workflows.
Run drift checks locally.
Terraform init
terraform plan -refresh-only -out=drift.planThis updates your state with live resource data and reports differences without applying changes.
It's a quick way to verify that your local state still matches the cloud state.
Automate in CI
Set up a nightly or hourly job to run drift checks:
terraform init -input=false
terraform plan -refresh-only -lock-timeout=10m -out=drift.plan
terraform show -json drift.plan > drift.jsonYou can then parse drift.json to notify your team in Slack or Jira when drift is detected.
However, CI-based detection comes with challenges:
• You need cloud credentials for every environment.
• Alerts are often noisy.
• The results lack context for what's risky vs. what's benign.
Detect drift pre-merge (the best approach)
The ideal approach is to detect drift before code merges.
This ensures your pull requests are based on an accurate infrastructure state.
Running drift checks at review time provides developers and reviewers with a clear picture of costs, security, and drift in one place.
Safe remediation patterns
- Update your Terraform code
If a manual change was valid, make it permanent by updating your Terraform configuration to match production, then re-run plan and apply. - Revert production to code
If the manual change was temporary, use Terraform to reapply your original desired configuration. - Import unmanaged resources
For resources created outside Terraform, bring them under management:
terraform import aws_iam_role.app_role app-role
Minimize downtime with lifecycle rules
Use create_before_destroy for safer replacements:
lifecycle {
create_before_destroy = true
}Add guardrails
Set policies for sensitive attributes (CIDRs, IAM permissions, encryption) to prevent recurring risky drift.
Troubleshooting drift noise
Not all drift is dangerous. Some comes from harmless ephemeral fields or evolving APIs.
Common patterns:
• Drift not detected: Upgrade provider or check provider schema coverage.
• Drift keeps returning: Another system (like CloudFormation) is mutating resources.
• Tag drift: Refine tagging policies rather than ignoring all tags.
• Ephemeral attributes: Document and exclude fields like timestamps or last modified dates.
Operating Terraform at scale
In large orgs, drift compounds across hundreds of workspaces and repos.
• Standardize workspaces - consistent naming, backends, and provider versions.
• Use central identity and state management - OIDC auth for cloud providers.
• Aggregate drift reports - dashboards by team, environment, and severity.
• Codify best practices - use opinionated modules that enforce secure, consistent defaults.
⸻
Drift, blast radius, and cost
- Drift isn't just technical debt; it creates risk and waste.
Security risk
- Opened security groups, disabled logging, and unencrypted data.
Operational risk
- Route misconfigurations, broken dependencies, or missing health checks.
Cost Impact
- Oversized instances, duplicated NAT gateways, unused volumes.
Effective drift detection should answer:
- What changed?
- What does it impact?
- What will it cost?
- How do we fix it safely?
Shift-left drift: pre-merge automation with Terracotta AI
Most teams eventually try to script drift checks, run refreshes, parse JSON, and comment on PRs. It's functional but brittle. What's missing is context and trust.
Terracotta AI integrates directly into your GitOps workflow to automate this entirely.
It analyzes uses natural language AI Guardrails within Terraform pull requests using live infrastructure context to detect and explain:
- State drift between code, state, and cloud resources
- Security and compliance risks like public S3 or unsafe IAM roles
- Cost deltas for new or resized resources
Dependency conflicts that could break downstream services
When drift is detected, Terracotta generates plain-language summaries directly in your PR:
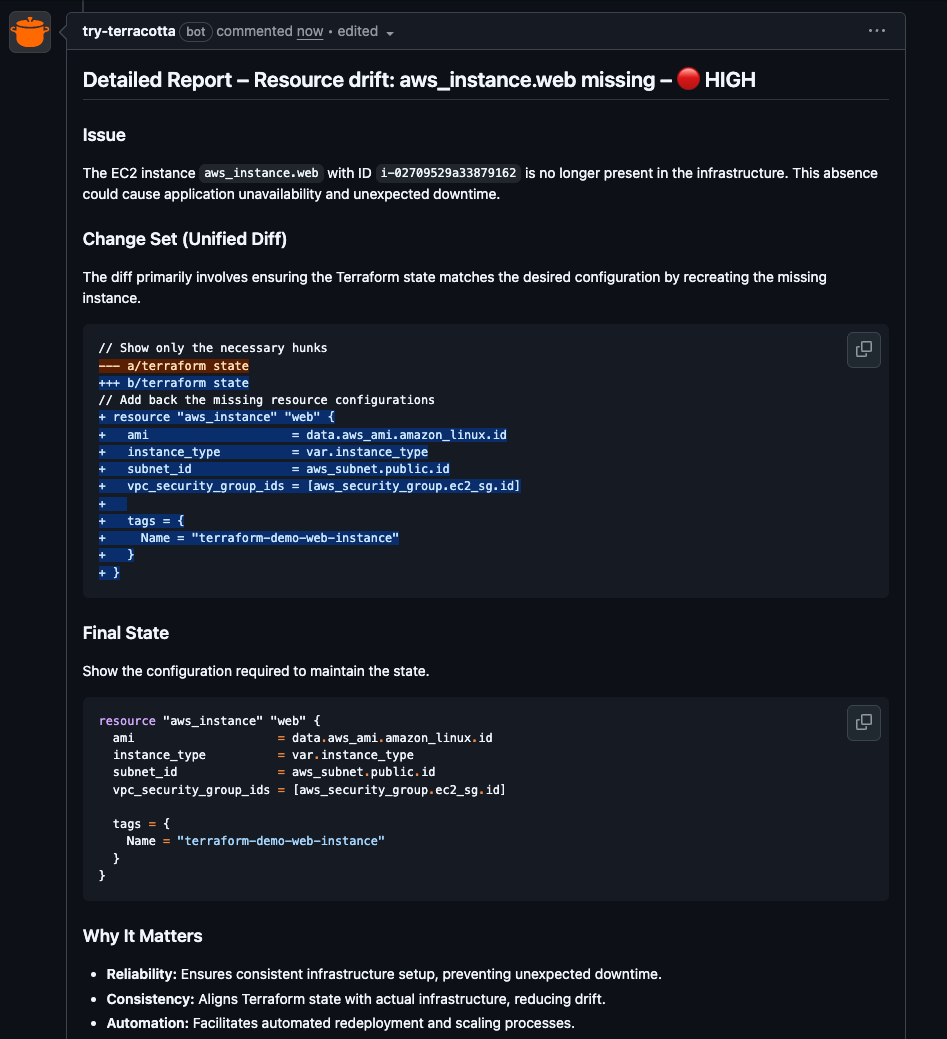
No guesswork. No manual refreshes. No extra CI jobs.
Terracotta fits directly into your existing GitHub or GitLab flow, with no new runners, no custom scripts, and no vendor lock-in.
Remediate confidently
When Terracotta AI flags drift, you can:
• Simulate how Terraform apply would behave without executing it.
• Identify who caused the drift and when.
• Prevent future drift by enforcing policies before the merge.
Drift goes from an afterthought to a preventable, explainable, and auditable part of your review process.
Key takeaways
- Drift is inevitable; undetected drift is dangerous.
- Lock state, minimize console changes, and limit ignore_changes.
- Manual drift checks are noisy and reactive.
- Terracotta AI brings real-time, context-aware drift detection straight into pull requests, giving platform teams control without friction.
Terracotta AI is building AI-native IaC guardrails for platform teams and their Infrastructure-as-Code deployment pipelines. Our natural language AI guardrails for platform teams easily create and enforce standards, security, and cost control in every Terraform pull request.
If you want to stop firefighting drift and start governing it:
👉 Start reviewing up to 20 Terraform and CDK-TF PRs for free. No CC required.


Comments ()