Why is Terraform still hard in 2025?
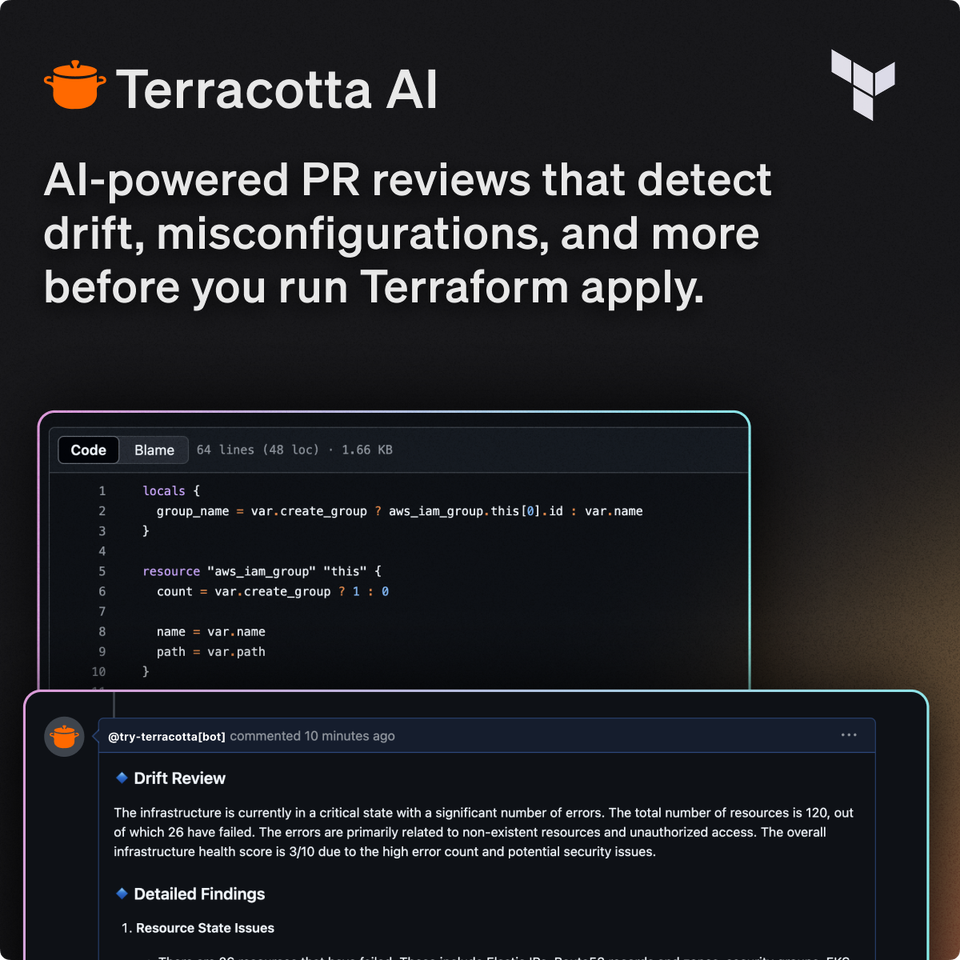
Hashicorp's Terraform has been around for over a decade. It’s the most popular Infrastructure as Code tool. It’s declarative, GitOps-friendly, and supposed to be safe.
You might think that writing and managing Terraform would be straightforward by now. You’d assume we’ve ironed out the workflows, nailed the best practices, and wrapped it all in tools that just Work.
If that’s been your experience, please reach out. We’d love to learn your secrets — and we’ll bring snacks.
Terraform in practice
We’ve worked with and spoken to platform teams at fast-moving startups, growing mid-size orgs, and multi-cloud enterprises. They all use Terraform and have built internal tooling, standards, and CI pipelines to manage it.
And almost all of them still have the same problems: drift, copy-paste modules, fragile reviews, broken dependencies, unclear ownership, and too much tribal knowledge.
Everyone’s following “best practices,” yet everyone’s experience still feels brittle.
Let’s dive in.
Problem 1: Terraform is deceptively simple
“I just need to provision an S3 bucket and an IAM role. Shouldn’t take more than 10 minutes.”
– Famous last words from a junior engineer
Terraform starts easy. But what you see is only the top of the HCL iceberg.
You write a few resources. Then you need a backend. Then providers. Then variables. Then modules. Then environments. Then workspaces. Then you realize the code is the easy part, and the real complexity is in understanding what this code will actually do in the real world.
Every team writes layers of wrapper scripts, CI pipelines, plan parsers, and approval flows to make Terraform usable at scale. There are tools to run it, format it, lint it, and gate it.
At some point, you’re not even writing infrastructure anymore. You’re just managing the machine that manages the machine.
Problem 2: Everyone’s Terraform is different!
The beauty of Terraform is its flexibility. The curse of Terraform is also its flexibility.
Every company has its own flavors:
- Custom modules with their own naming patterns, output conventions, and hidden assumptions
- Some teams use
terraform apply; others have 8-step CI workflows - Some apply per environment, some per resource, some per team
- Half the team uses Terragrunt (wrong), the other half doesn’t (also wrong)
We've seen orgs where three different environments use three different state backends, where the same module name means three totally different things, and where no one can say for sure which AWS account owns a given resource.
Terraform isn’t a tool anymore — it’s folklore.
Problem 3: Drift is inevitable
The moment your infrastructure touches the real world, it starts to drift.
→ An engineer fixes something manually in the AWS console.
→ Someone disables a policy to unblock a deploy.
→ An external system updates a tag.
→ A resource gets destroyed and recreated with new defaults.
You run terraform plan and it looks fine — because Terraform only knows what you told it. It doesn’t know about the out-of-band changes. It doesn’t warn you that a resource has drifted. It happily wipes out your fix and calls it “safe.”
Most teams don’t know there’s drift until it breaks production. And even then, the plan still looks green.
Problem 4: The plan looks fine. Until it isn’t.
Terraform plans are supposed to bring safety and predictability.
In theory, you see what will change before it changes.
In practice: You scroll through hundreds of lines, looking for anything suspicious, hoping nothing sneaky gets through.
The plan tells you what will change. It rarely tells you why.
It doesn’t tell you what modules depend on this.
It doesn’t tell you which services this IAM policy might break.
It doesn’t tell you this change will wipe out and recreate a stateful database.
Most reviews are written by people who didn’t write the original infra, don’t know the blast radius, and just want to keep the deployment moving.
So people hit “approve” and hope for the best.
Problem 5: Debugging Terraform is a black box
When something breaks, Terraform gives you this:
Error: Invalid indexOr worse:
Error: object requiredHelpful.
You trace through nested modules, try to remember if that variable is a string or a map, and mentally reconstruct the dependency tree. You check the state. You re-run the plan. You eventually just console.log your way through terraform console.
Terraform doesn't make debugging easy. It makes you guess.
Problem 6: Infra review doesn’t scale
In theory, Terraform should enable fast, safe infra changes.
In practice, infra PRs sit for days because:
- No one has enough context to approve them confidently
- Everyone is afraid of breaking something
- The person who owns the module is on PTO
- The plan is massive, and no one wants to read it
The result? You either block product teams or approve blindly.
Neither is good. Both are common.
Some things we haven’t even mentioned yet
We haven’t talked about:
- Plan noise from computed diffs
- Implicit vs. explicit dependencies
- Hidden resource recreation
- Conditional logic that breaks silently
- The tension between DRY and readable code
- Running
terraform destroyin the wrong workspace 😬
A better way?
If you’ve read this far, you’re probably not surprised by any of this. You’ve lived it. Terraform gives you control, but it doesn’t provide you with confidence.
Not when drift is invisible.
Not when context lives in someone’s head.
Not when reviewing a plan feels like decoding a black box.
Infra isn’t hard because we’re doing it wrong.
It’s hard because the workflows weren’t designed for how teams actually build and ship today: fast-moving, multi-owner, highly parallel, deeply interconnected.
Terracotta AI is our attempt to fix that.
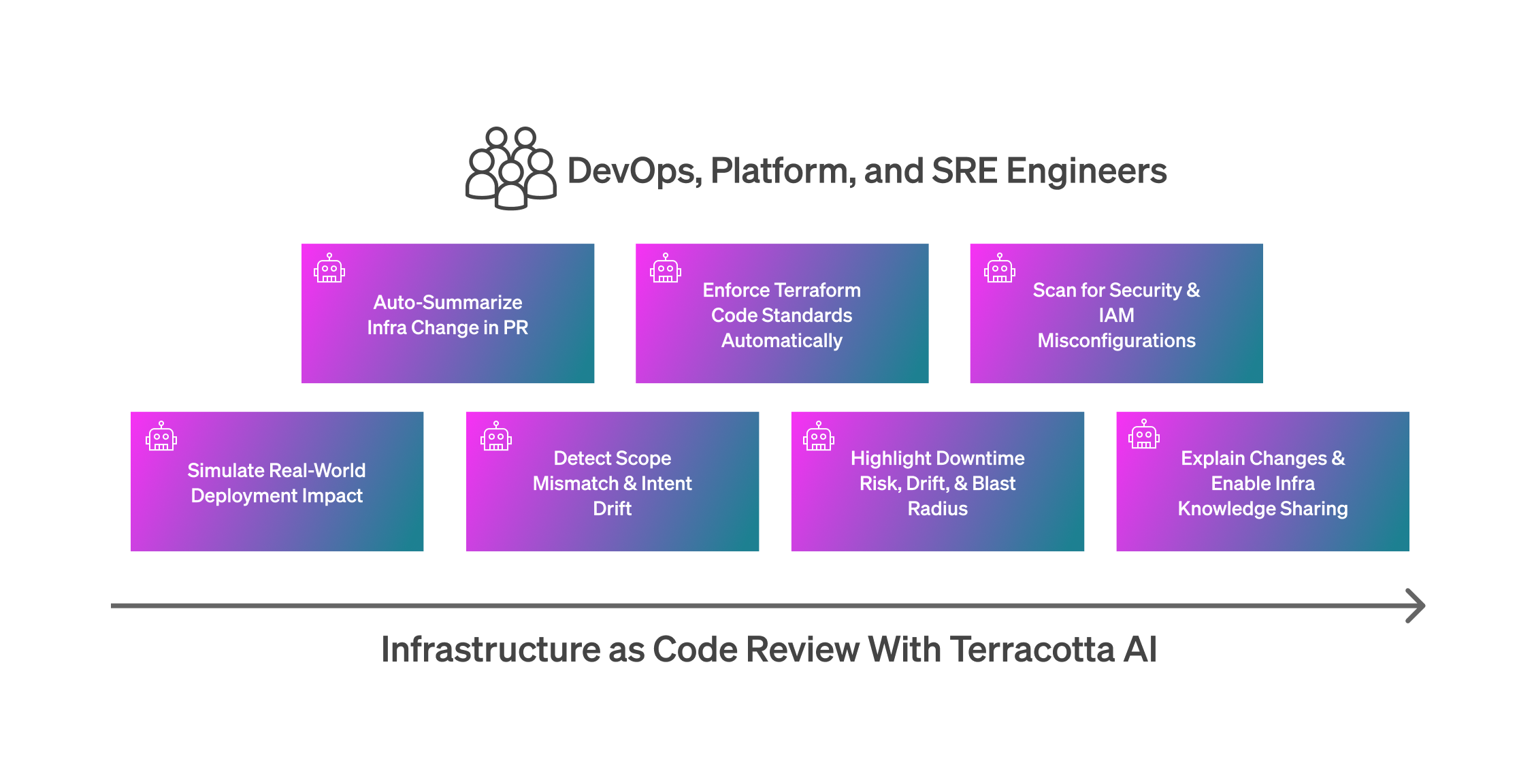
We plug into your entire deployment pipeline, including the remote state and live-running infrastructure, to bring real context into your Terraform workflow directly to your Terraform pull requests or merge requests—surfacing drift, tracking dependencies, highlighting risk, and making every change reviewable with confidence.
No more guessing. No more surprises.
Just infrastructure you can trust.



Comments ()